Jul 04, 2006 Concerning the virus W97M/downloader obtained via my latest Microsoft Office for Mac MAU: (build 19081202, v16.28.0)-my Intego AV detected 1,015 Trojans which had attached themselves to most of the files in my docs folder. A recent backup fixed it but now I don't trust the MAU.
I have Norton Internet Security on a Lenovo desktop with Windows 7. Lately, sometimes when I perform a full system scan, NIS finds W97M.Downloader, sometimes more than one instance of it, which NIS labels as 'quarantined'. My question: Why doesn't NIS intercept and delete W97M.Downloader when it first arrives on my desktop (with email I presume)? What would happen if I were not to run a full system scan regularly? Once, after a full system scan, NIS seemed to have found W97M.Downloader, but not quarantined it. I went to Norton's website, and there learned that I should go into Safe Mode, run a full scan, and then delete W97M.Downloader, which I did. I have been using Norton utilities since the days of Peter Norton and DOS. This is the first time that Norton does not seem to me to be functioning sensibly (reassuringly). Am I missing something? Thank you.
- W97M is a windows (specially it is a Word Macro virus), it is harmless on a Mac, Norton is your problem, it is useless, and it will cause problems with the Macs performance and stability, and it will needlessly scare the user. As you are now seeing.
- W97M.Downloader is malicious software that can secretly act against the interest of the affected user. Once inside the system, W97M.Downloader can keep track of keystrokes, thereby stealing sensitive user information such as passwords and login credentials. The W97M.Downloader Virus detected by multiple antivirus programs.
- The detection 'W97M.Downloader.variant' identifies malicious macro code embedded in a Microsoft Word document file.This file is usually distributed as an attachment to an email message. The 'bait' Word document file will typically be crafted to look legitimate and appealing to a user (for example, pretending to be a resume or containing interesting news items or content), so that they are.
McAfee Labs recently found a variant of the W97M macro malware downloader that runs the Vawtrak malware. Although W97M usually employs Microsoft Office documents to run malicious Visual Basic scripts that download and run malware, this instance of W97M contains an embedded executable that is dropped onto the file system using a malicious macro.
W97M is a malware family comprising all malicious Office files (rich text, Word, Excel, etc.) that rely on macros containing VB scripts to download and run a specific malware from its control servers. Recently McAfee Labs has seen multiple waves of W97M malware serving malware, especially:
- Ransomware such as TeslaCrypt and Locky.
- Banking Trojans such as Dridex.
Vawtrak is a multifunctional malware family with the following capabilities:
- Stealing FTP passwords from a victim’s system.
- Stealing certificates from a victim’s system.
- Stealing credentials and other information via process infection.
- Malicious code injection in web pages displayed in a browser on a victim’s system.
- Running arbitrary commands on a victim’s system.
Infection vector and analysis
W97M malware is usually served via malicious email spam campaigns. This instance of W97M, however, is served from compromised websites. These compromised websites might be used with exploit kits or phishing campaigns that trick victims into downloading and running the W97M documents.
Some URLs serving the W97M malware:
- hxxp://www.excel-dougakaisetu.com/wordpress/wp-content/plugins/[masked]/account.doc
- hxxp://www.ippan.x0.to/wp-content/themes/[masked]/account.doc
- hxxp://www.newbeginningsari.org.au/wp-content/[masked]/account.doc
- hxxp://www.sternschule-uelzen.de/wp-content/plugins/[masked]/account.doc
- hxxp://elveland.no/wp-content/themes/[masked]/account.doc
- hxxp://www.nightaccess.com/themes/[masked]/account.doc
- hxxp://excel-dougakaisetu.com/wordpress/wp-content/plugins/[masked]/account.doc
- hxxp://nightaccess.com/themes/[masked]/account.doc
- hxxp://www.paintballandbbthailand.com/modules/[masked]/account.doc
- hxxp://ippan.x0.to/wp-content/themes/[masked]/account.doc
- hxxp://www.elveland.no/wp-content/themes/[masked]/account.doc
- hxxp://paintballandbbthailand.com/modules/[masked]/account.doc
- hxxp://sternschule-uelzen.de/wp-content/plugins/[masked]/account.doc
- hxxp://www.yacht-energy.fr/wp-content/themes/[masked]/account.doc
The W97M sample appears to have an RSA-encrypted message embedded in its contents. The document asks the victim to “enable content” to view the decrypted contents of the document. This is a standard trick to get the victim to enable the malicious macro, which drops an embedded executable and executes it.
Contents of a malicious W97M document.
The document contains the malicious .exe embedded inside one of its forms. We have seen other examples of W97M embedding commands in forms but not as in the preceding example, in which the entire .exe is embedded in the document.
Embedded .exe in a Visual Basic form.
The malicious macro reads the contents of the form and writes it into an executable in the %temp% directory.
Malicious macro code in the W97M malware.
Second-stage executable
The executable dropped in the %temp% directory is a VB 6 binary. The code is decrypted at runtime and the malware creates a suspended copy of itself that is injected with the malicious code. This malware is a variant of Pony malware.
The primary functions of the second-stage binary:
- Steal FTP and other login credentials from known FTP software.
- Download and run the third-stage binary (Vawtrak).
Strings in the second-stage malware indicate the theft of FTP credentials.
Once the second-stage binary has all the credentials it can find, it sends the stolen data to the following control servers:
- hxxp://tittertte.ru/sliva/gate.php
- hxxp://tythetru.ru/sliva/gate.php
- hxxp://rulahat.ru/sliva/gate.php
These domains appear to be under the attacker(s) control:
- They are registered with the same registrar with registrant information hidden.
- They were registered on the same dates.
- They expire on the same dates.
This malware targets the following software for credentials:
- Far Manager
- Total Commander
- Ipswitch WS_FTP
- CuteFTP
- FlashFXP
- FileZilla
- FTP Navigator
- Bulletproof FTP
- Smart FTP
- Turbo FTP
- FFFTP
- FTP++
- GoFTP
- Cofeecup FTP
- CoreFTP
- FTP explorer
- LeapFTP
- WinSCP
- 32BitFTP
- ClassicFTP
- SoftX FTP client
- UltraFXP
- FTPRush
- FTPControl
- FTPVoyager
- LeechFTP
- Estsoft ALFTP
- DeluxeFTP
- Staff FTP
- FTP Visicom Media
- AceBit WiseFTP
- FreshFTP
- BlazeFTP
- 3D-FTP
- EasyFTP
- Winzip FTP
- WinFTP
- FTPSurfer
- FTPGetter
- FTPNow
- Robo-FTP 3.7
- Linas FTP Site Manager
- Notepad++ FTP
- Coffeecup ftp profile
- FTPShell
- MyFTP
- NovaFTP
- Yandex
- Adobe Common SiteServers
- Frigate3
- SecureFX
- Cryer WebsitePublisher
- BitKinex
- ExpanDrive
- NCH Software Fling
- Directory Opus
- NetDrive
- Webdrive
- Opera
- Firefox
- Firefox FireFTP
- Mozilla Seamonkey
- Mozilla Flock
- Mozilla Profiles
- SiteInfo.qfp SpeedFTP
- Chrome login and web data
- Chromium login and web data
- Chrome plus login and web data
- Bromium login and web data
- Nichrome login and web data
- Comodo login and web data
- RockMelt login and web data
- K-Meleon profile data
- Epic profile data
- GlobalDownloader
- NetSarang
- RDP
- CyberDuck
- Putty
- MAS Soft FTPInfo
- NexusFile
- FastStone Browser FTPlist
- MapleStudio Chromeplus
- Windows Live Mail
- Windows Mail
- RimArts Mail
- Pocomail
- Incredimail
- BatMail
- MS Internet Account Manager
- Thunderbird
Once the second-stage malware has uploaded the stolen credentials to the control server, it downloads the third-stage malware from a different set of control servers and runs it:

- hxxp://awc.asia/wp-content/themes/[masked]/hsg.exe
- hxxp://teatromanzonicassino.it/wp-content/themes/[masked]/hsg.exe
- hxxp://www.bisaim.com/wp-content/themes/[masked]/hsg.exe
Third-stage executable
The third-stage executable is the Vawtrak payload (also a VB 6 binary).
The primary purpose of the binary is to infect other running processes in the system and:
- Steal security certificates.
- Infect Chrome and Firefox processes to inject malicious code into browsed web pages.
- Steal financial login credentials for banks.
Process infection and API hooking
W97m Downloader Mcafee
The malware spreads across the system by injecting its code into any process that doesn’t appear on the following whitelist:
- csrss.exe
- smss.exe
- wininit.exe
- services.exe
- svchost.exe
- lsas.exe
- lsm.exe
- winlogon.exe
- dbgview.exe
- taskhost.exe
The malware also looks for the following processes to establish API hooks:
- Internet Explorer
- HttpEndRequest, HttpOpenRequest, HttpQueryInfo, HttpSendRequest,
- InternetConnect, InternetQueryDataAvailable, InternetQueryOption, InternetReadFile.
- Firefox
- PR_Close, PR_Read, PR_Write, PR_Close, etc.
- Chrome
- LoadLibrary, PFXImportCertStore, etc.
- Other processes
- CreateProcessInternal: To infect any new process spawned by this process.
- PFXImportCertStore: To steal certificate information from the victim.
API hooks established by the third-stage malware.
The malware uploads the stolen data to one of the following control servers:
- castuning.ru/rss/feed/stream
- mgsmedia.ru/rss/feed/stream
- puropea.com/rss/feed/stream
- futooke.com/rss/feed/stream
- citroxi.com/rss/feed/stream
Infection chain
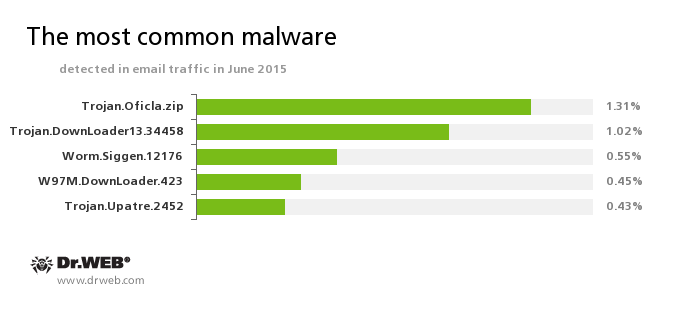
The stages of infection are illustrated in the following figure:
Anti-VM measures
Both the second- and third-stage binaries of Vawtrak check the monitor resolution using User32.GetMonitorInfoA to make sure the malware isn’t running in a virtual machine. The malware binaries check to make sure the monitor resolution is greater than 800×600. This technique is employed to thwart some behavior-based detection systems.
Vawtrak’s monitor-resolution check.
Conclusion
This W97M malware differs from typical W97M malware due to the embedded binary inside the document. This tactic could be a result of the increased focus in the security community on W97M and the subsequent blacklisting of its control servers. Embedding an .exe in the doc file removes the need to contact a control server to download and execute the second-stage malware.
The encryption mechanisms and the use of VB 6 in both the second and third stages indicate that both instances of the malware share a common codebase, suggesting they could have been written by the same party.
MD5s
W97m Downloader Mac Free
W97M samples. These samples are detected by McAfee as “W97M/Dropper.ao.”
- e56a57acf528b8cd340ae039519d5150
- 040c51e8c9118cc113c380d530984ba8
- ef10ea1a8b342dd9f6d1cec46fcd3c0f
Second-stage malware: These samples are detected as “Generic.xy.”
- 4b7623945d31ecd6ff1ed13f0ba1d6e0
Third-stage malware: These samples are detected as “RDN/Generic.cf” and “Vawtrak-FBB.”
- 3e631d530267a38e65afc5b012d4ff0c
Yara rule for W97M Vawtrak dropper
rule W97M_Vawtrak_dropper
{
meta:
author=”McAfee”
description=”W97M_Vawtrak_Dropper”
strings:
$asterismal=”asterismal”
$bootlicking=”bootlicking”
$shell=”WScript.Shell”
$temp=”%temp%”
$oxygon=”oxygon.exe”
$saxhorn = “saxhorn”
$fire = “Fire”
$bin= “546869732070726f6772616d2063616e6e6f742062652072756e20696e20444f53206d6f64652e”
Virus W97m Downloader
condition:
all of them
}